Phases of insider threat recruitment include a series of distinct stages through which threat actors attempt to recruit individuals within an organization to carry out malicious activities. Understanding these phases is crucial for organizations seeking to prevent and mitigate insider threats.
This article delves into the intricacies of insider threat recruitment, exploring the initial phase, grooming phase, and exploitation phase. It also discusses indicators of insider threat recruitment, methods of prevention, and case studies of successful recruitment campaigns.
Phases of Insider Threat Recruitment
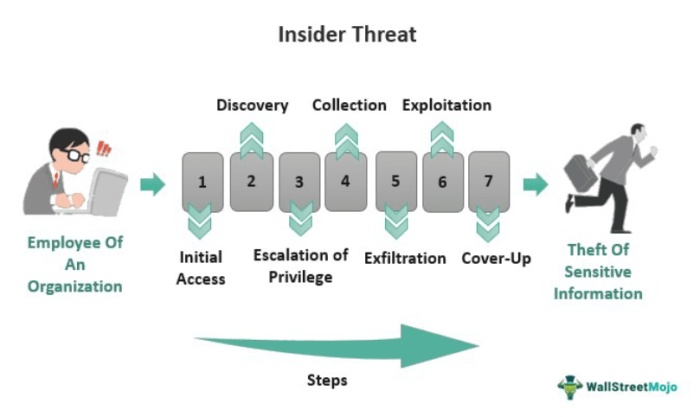
Insider threat recruitment is a multi-stage process involving various tactics and techniques. Understanding these phases is crucial for organizations to prevent and mitigate insider threats.
Initial Phase
The initial phase involves identifying potential targets and establishing initial contact. Threat actors may use social media, email phishing, or other methods to gather information and engage with individuals who have access to sensitive information or systems.
Grooming Phase
In the grooming phase, threat actors build trust and rapport with the target individual. They may use flattery, attention, or other forms of manipulation to gain the target’s confidence and willingness to share information or assist in malicious activities.
Exploitation Phase
Once the target is sufficiently groomed, the threat actors exploit their vulnerabilities and weaknesses. They may pressure the target to perform unauthorized actions, provide sensitive information, or compromise systems for personal gain or to benefit the threat actor’s organization.
Indicators of Insider Threat Recruitment
Recognizing the early signs of insider threat recruitment is essential for prevention. Potential indicators include:
Behavioral Changes
- Unusual interest in sensitive information or areas
- Increased communication with external parties
- Changes in work patterns or responsibilities
Communication Patterns
- Increased use of encrypted communication channels
- Attempts to conceal or delete emails or messages
- Unusual patterns of communication with known or unknown individuals
Social Media and Online Interactions
Monitoring social media and online interactions can reveal potential indicators, such as:
- Sharing sensitive information or company secrets
- Engaging with individuals known to be involved in malicious activities
- Posting about financial or personal difficulties
Methods of Insider Threat Recruitment Prevention: Phases Of Insider Threat Recruitment Include
Organizations can implement proactive measures to prevent insider threat recruitment:
Security Awareness Training
Educating employees about potential threats and recruitment tactics is crucial. Training should emphasize:
- Recognizing and reporting suspicious behavior
- Protecting sensitive information and systems
- Maintaining professional boundaries
Insider Threat Detection and Response Plan
Developing and implementing a robust insider threat detection and response plan is essential. This plan should include:
- Clear procedures for reporting suspicious activity
- Processes for investigating and responding to incidents
- Mechanisms for monitoring employee behavior and online interactions
Case Studies of Insider Threat Recruitment

Analyzing real-world case studies provides valuable insights into the tactics and techniques used by threat actors.
Case Study: The Boeing Employee
In 2018, a Boeing employee was recruited by Chinese intelligence to provide sensitive information about the company’s military aircraft programs. The employee was groomed over several months through a combination of flattery and financial incentives.
This case highlights the importance of monitoring employee communication and social media activity, as well as conducting thorough background checks.
Case Study: The SolarWinds Attack, Phases of insider threat recruitment include
In 2020, the SolarWinds software supply chain attack compromised the systems of numerous government agencies and private companies. The attack was initiated through the recruitment of an insider at SolarWinds, who provided access to the company’s network and software.
This case demonstrates the devastating impact of insider threats and the need for robust security measures throughout the supply chain.
Question & Answer Hub
What are the key phases of insider threat recruitment?
The key phases of insider threat recruitment include the initial phase, grooming phase, and exploitation phase.
How can organizations prevent insider threat recruitment?
Organizations can prevent insider threat recruitment through proactive measures such as security awareness training, background checks, and monitoring employee behavior.
What are some indicators of insider threat recruitment?
Indicators of insider threat recruitment include behavioral changes, suspicious communication patterns, and unexplained access to sensitive information.